Managed Cybersecurity
MSP Verify Certified ✓
As an MSP Verify and Cyber Verify AA certified provider, customers of Data Networks can rest assured that they're working with an IT service provider that prioritizes experience, accountability, and professionalism.
The MSP Verify certification by MSPAlliance is the most trusted, independently audited program for Managed IT & Cloud Service Providers worldwide.
Features of our Managed Cybersecurity
You'll have access to an entire team of skilled professionals with specialized knowledge and experience in preventing and assessing security threats. We use the latest techniques and technologies to keep you safe, plus provide insights, guidance, and education that will keep your organization ahead of the curve.
You can rely on us to:
- Identify and respond to potential security threats
- Streamline compliance with regulatory requirements
- Help ensure your organization follows cybersecurity best practices
- Dramatically decrease the chances and potential impact of a security event and provide evidence of due diligence
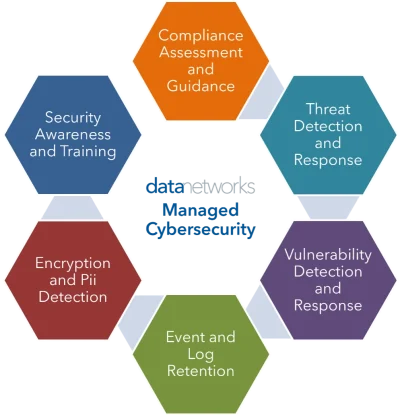
- Mitigate risk by monitoring, analyzing, and managing 6 critical areas of your IT environment:
1. Compliance Assessment and Guidance
2. Threat Detection and Response
3. Vulnerability Detection and Response
4. Event and Log Retention
5. Encryption and Pii Detection
6. Security Awareness and Training

| What It Is | Policy assessment and recommendations for all relevant standards plus cyber liability insurance. |
| Threats Addressed | Vulnerabilities and potential penalties due to non-compliance. |
| Features | Policy assessment, risk analysis, and recommendations as part of onboarding, then 1x per year. |
| Deliverables | AV status report; user access report; asset and application inventory; compliance worksheet. |

| What It Is | Expert team who monitors your environment to prevent, detect, and respond to threats. |
| Threats Addressed | Intrusions; malware attacks; ransomware attacks. |
| Features | 24/7 proactive threat monitoring across endpoints, network, and cloud; automatic isolation of clients to facilitate remediation. |
| Deliverables | Monthly SOC report. |

| What It Is | Scanning and reporting that identifies and evaluates the severity of security vulnerabilities and misconfigurations that could be exploited by attackers. |
| Threats Addressed | Vulnerabilities in networks, operating systems, applications, and other systems such as missing patches, outdated software, configuration issues, open ports, unsecured services, weak password. |
| Features | Monthly scans; quarterly report with recommendations based upon severity. |
| Deliverables | Quarterly reporting with analysis and recommended actions. |
| What It Is | Collects and stores log and security event data generated by an organization's operating system; manages the retention of logs; indexes logs for easy identification. |
| Threats Addressed | Simplifies access to logs for security analysis, compliance, and troubleshooting when needed. |
| Features | Syslog and storage with retention policy to match your needs; correlation; search and analysis. |
| Deliverables | Dashboard; monthly report. |

| Microsoft File and Email Encryption | |
| What It Is | System changes for automatic encryption to help ensure the confidentiality of sensitive information. |
| Threats Addressed | Data breaches; man-in-the-middle attacks; phishing attacks; insider threats; regulatory compliance. |
| Features | Enables the ability to flag sensitive information (MS Office labels) to automatically encrypt data. |
| Deliverables | Configuration plus training documentation. |
| Pii Detection | |
| What It Is | Scans OneDrive, email, and SharePoint files for personally identifiable information (social security number, financial information, medical records, etc.) |
| Threats Addressed | Potential identity theft; unauthorized access; social engineering; reputation damage. |
| Features | Discover, identify, and classify sensitive data; compliance and security settings in O365 tenant; setup Pii scans on OneDrive, mail, SharePoint. |
| Deliverables | Pii scan and report 12x per year (cloud and on-prem). |

| Employee Phishing | |
| What It Is | Phishing platform that delivers a personalized, simulated phishing experience to end users and track results. |
| Threats Addressed | Credential theft; malware infections; identity theft; reputation damage as a result of employee carelessness. |
| Features | Customizable phishing campaigns and landing pages; AI-driven personalized phishing experience for each user. |
| Deliverables | 6x campaigns per year; reports to monitor changes in phishing results over time. |
| Security Awareness Training | |
| What It Is | Self-paced employee training modules designed to increase security awareness and best practices. |
| Threats Addressed | Credential theft; malware infection; identity theft; reputation damage from employee carelessness. |
| Features | A different, personalized training module emailed to employees 4x per year. |
| Deliverables | Completion certificates; training results. |
Services Timing and Frequency
Our Managed Cybersecurity services are scheduled to provide maximum protection at an affordable cost. Every engagement begins with a compliance audit to assess your security posture and expands to include all services as outlined below:
| Services | Month | |||||||||||
| 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 | 11 | 12 | |
| Compliance Services | ||||||||||||
| SOC Services | ||||||||||||
| Vulnerability Assessment | ||||||||||||
| Event and Log Retention | ||||||||||||
| Microsoft Encryption (File and Email) | ||||||||||||
| Microsoft Pii Scans (M365) | ||||||||||||
| Employee Phishing Campaign | ||||||||||||
| Employee Cybersecurity Training | ||||||||||||
| Cybersecurity Newsletters | X | X | X | X | ||||||||
| Cybersecurity Webinars | X | |||||||||||
Services Timing and Frequency
Our Managed Cybersecurity services are scheduled to provide maximum protection at an affordable cost. Every engagement begins with a compliance audit to assess your security posture and expands to include all services as outlined below:
| Services | Month | |||||||||||
| 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 | 11 | 12 | |
| Compliance Services | ||||||||||||
| SOC Services | ||||||||||||
| Vulnerability Assessment | ||||||||||||
| Event and Log Retention | ||||||||||||
| Microsoft Encryption (File and Email) | ||||||||||||
| Microsoft Pii Scans (M365) | ||||||||||||
| Employee Phishing Campaign | ||||||||||||
| Employee Cybersecurity Training | ||||||||||||
| Cybersecurity Newsletters | X | X | X | X | ||||||||
| Cybersecurity Webinars | X | |||||||||||
The Data Networks Difference
Our holistic approach to managed IT services is unique and designed to help your organization operate at its best for one affordable monthly cost. All of our managed IT solutions include:

CENTRALIZED SERVICES
Our team proactive identifies potential problems and addresses them before they happen to ensure peak performance and uptime

SUPPORT
Call or email us for unlimited administrative and technical support with timely dispatch of on-site resources when required.

TECHNOLOGY ALIGNMENT
We use proven standards, careful documentation, and accepted best practices to ensure a consistent user experience.

STRATEGIC IT PLANNING
Your "virtual CIO" will work with you to proactively identify and address IT-related business risk and help you plan for needed improvements.
Add Managed Modules for enhanced protection
Managed Modules address your organization's needs that fall outside our core Managed IT Services offerings, each representing a managed service available as an add-on to your Managed Services contract at a reduced price.

Managed Module: BCDR
- Secure cross-platform protection
- Infinite cloud retention
- Ransomware vigilance and protection
- Operational resilience
- Reduced storage costs

Managed Module: Microsoft 365
- Administration of M365 ecosystem
- License plan recommendations
- Preventative monitoring, proactive maintenance, reactive issue support, and prompt troubleshooting
- Resources consumption reporting
- Consolidated monthly billing

Managed Module: SaaS Protection
- Coverage of data in all M365 and G Suite applications
- Protection against all types of data loss
- Quick recovery from cloud data loss regardless of cause
- Secure cloud-to-cloud backup (3X daily)
- Support for compliance efforts and security requirements

Managed Module: Network as a Service
Explore our other core Managed IT Services offerings
In addition to our Managed Cybersecurity, we also offer Fully Managed and Co-Managed IT Services, designed to fit the way you do IT. Learn more about each core offering below to determine which best suits your organization’s needs.

Fully Managed IT Services
If you “own” IT but have few or no internal resources to support it, Fully Managed IT Services offering is the right choice for you. Rather than going it alone, let our team of professionals become your expert IT department.

Co-Managed IT Services
You’ll get the same end-to-end management as our Fully Managed IT Services offering, minus computer and phone system support.
Manage Less, Innovate More!
Outsourcing your IT to Data Networks’ Managed IT Services means you’ll have access to an entire team focused on IT efficiency, plus ongoing guidance to help you realize your IT vision. So you can be sure your IT meets today’s needs while evolving to address tomorrow’s challenges.













